...
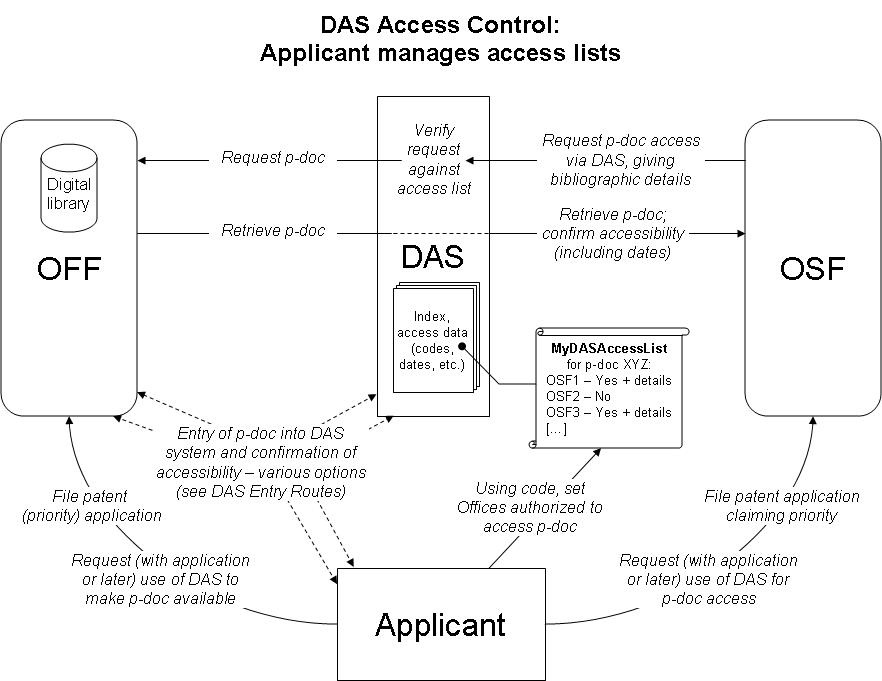
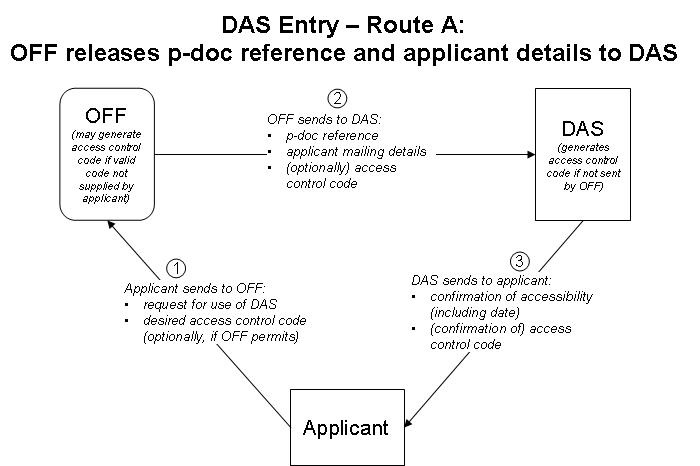
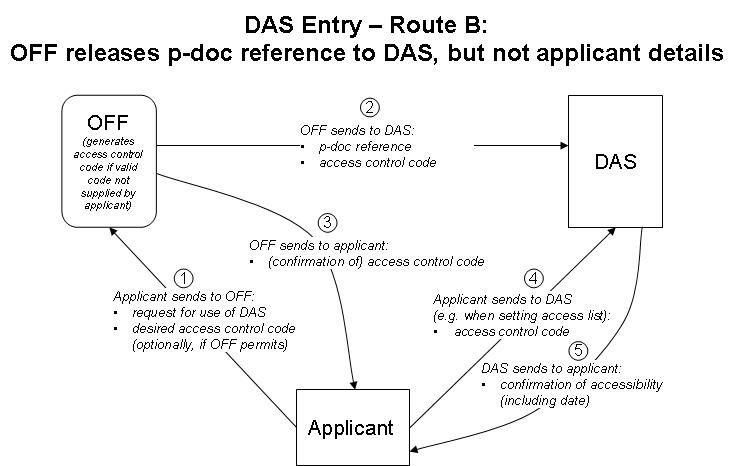
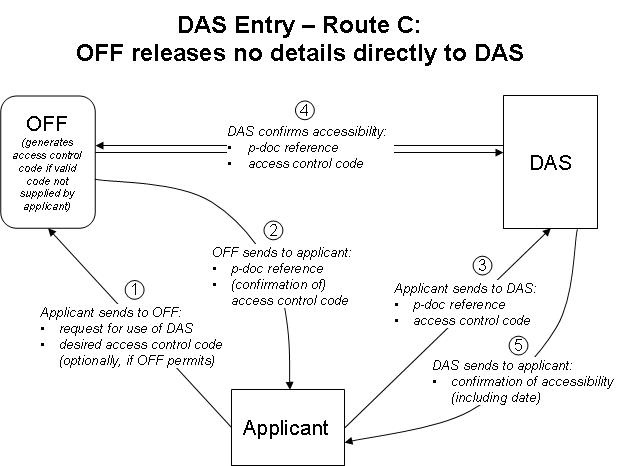
3. Document access control should be by a "managed access list" as described below and illustrated in Figure 1. In this system, on requesting that an application that may later form the basis for a priority claim be made available through DAS, the applicant is allotted an access control code specific to the application. The system should support several different routes for entry of priority documents into the DAS system, allowing for different legal constraints and user requirements, as detailed below in paragraphs 8 and 9 and Figures 2 to 4. The system should allow applicants to modify the access control code and the access control list using DAS at any time, provide a means for applicants to authorize the disclosure of sufficient information to DAS (as would be needed in the case of certain Offices such as the United States Patent and Trademark Office), and provide to the OSF information on the dates that a priority document became available to DAS, and when the applicant authorized access to that OSF.
Figure 1
4. Using the application number and the allotted code, the applicant can control which OSFs are permitted access to the application as a priority document by means of adjusting the settings in an access control list held in DAS by the International Bureau. This would normally be done directly by the applicant using a web interface, but for applicants with no Internet access, the International Bureau, or an Office of first filing which offers such a service, would set the details on request by post including the required information.
...
10. The security of the system also requires that the identity of Offices offering digital libraries or attempting to access a priority document be confirmed. However, this does not require special consideration because, whereas the identity of a person claiming to be an applicant is difficult to verify, the Offices involved are a limited group with which the International Bureau already has trusted communication channels. Each of the systems which are proposed to be used for communications already includes a means for establishing a secure channel between the International Bureau and a point which can be identified as a particular Office.
Figure 2
Figure 3
Figure 4