1. The system architecture should follow the network model shown in the conceptual diagram in the general principles, offering a gateway to a variety of Offices' digital libraries, some of which might also be accessible to some Offices by means other than the digital access service (DAS). It should permit certified copies of priority documents to be provided to DAS by the Office of first filing (OFF), directly by applicants, or by other Offices participating in DAS. It should offer a flexible combination of packaging channels and document formats, as indicated in paragraph 3 of the general principles.
2. The access control system is set out below. The system is set out in terms of actions before an OFF, but in fact it would work in the same way where the relevant digital library is maintained by any Office which holds a certified copy of the priority document (for example, as an OSF), supplied by an agent or applicant for which the Office has a name and address and is therefore able to send the access control code to a person who is known to have the right to make use of the document.
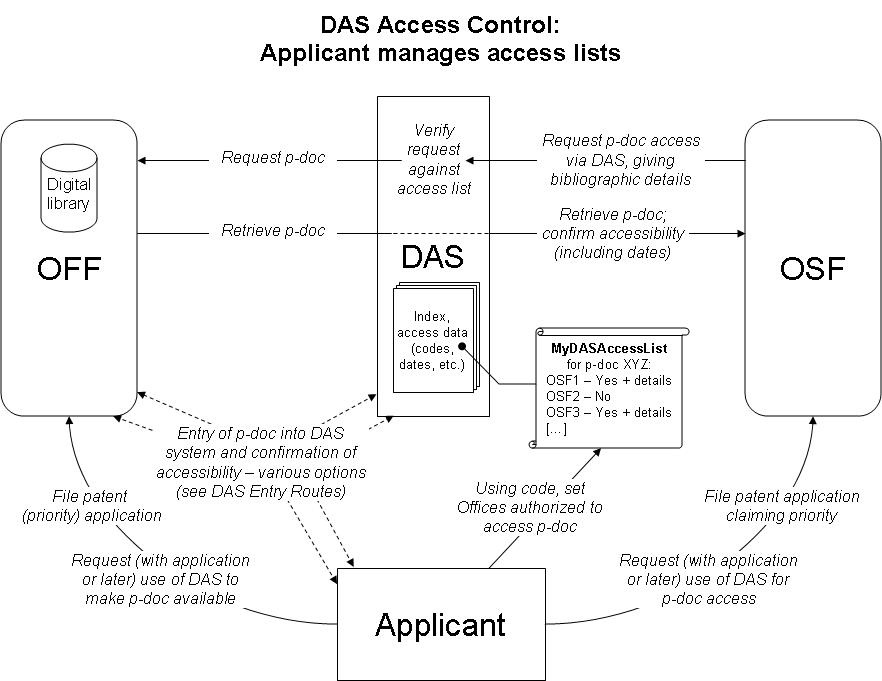
3. Document access control should be by a "managed access list" as described below and illustrated in Figure 1. In this system, on requesting that an application that may later form the basis for a priority claim be made available through DAS, the applicant is allotted an access control code specific to the application. The system should support several different routes for entry of priority documents into the DAS system, allowing for different legal constraints and user requirements, as detailed below in paragraphs 8 and 9 and Figures 2 to 4. The system should allow applicants to modify the access control code and the access control list using DAS at any time, provide a means for applicants to authorize the disclosure of sufficient information to DAS (as would be needed in the case of certain Offices such as the United States Patent and Trademark Office), and provide to the OSF information on the dates that a priority document became available to DAS, and when the applicant authorized access to that OSF.
Figure 1
4. Using the application number and the allotted code, the applicant can control which OSFs are permitted access to the application as a priority document by means of adjusting the settings in an access control list held in DAS by the International Bureau. This would normally be done directly by the applicant using a web interface, but for applicants with no Internet access, the International Bureau, or an Office of first filing which offers such a service, would set the details on request by post including the required information.
5. When the later application claiming priority is made (or at a later time when an applicant seeks to satisfy the priority document requirements after filing), the applicant would only need to state to a participating OSF that the priority document should be retrieved from DAS. The OSF would not require any information beyond the standard bibliographic details currently provided when making a priority claim in order to access the priority document, provided that access by that OSF had been authorized on the access control list within DAS for that priority document.
6. It should be noted that the step of authorizing access will be an essential one. Unless the applicant has set the authorization or the system recognizes that the document has already been published, the OSF will not be able to access the priority document through the system and rights might potentially be lost.
7. Possible future developments might include an "account" system, where an applicant who files many applications will be able to set a "default" access list, but this would not be part of the system to begin with in order to minimize costs and the time needed to deploy a basic working system.
Entry of priority documents into the DAS system; Allocation or confirmation of access control codes
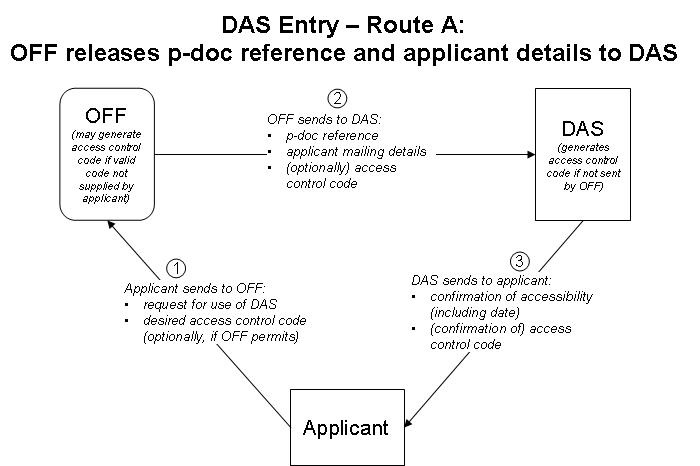
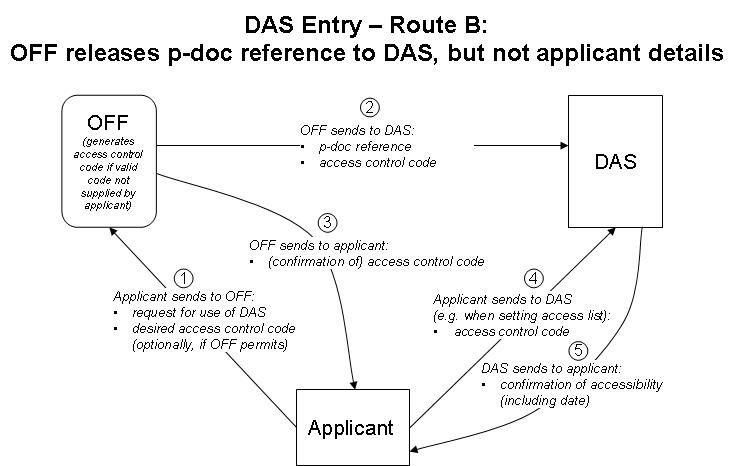
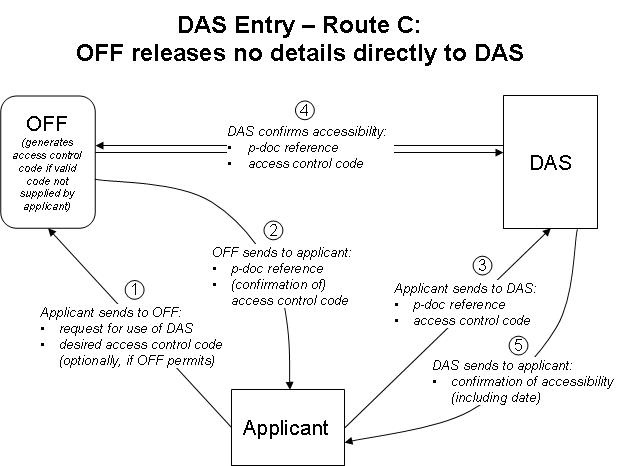
8. The system will need to work with digital libraries held by Offices which act under different legal constraints in relation to the confidentiality of applications and applicant details. It seems to be necessary to deal with three possible routes, illustrated in Figures 2, 3 and 4, below:
(a) Route A: The OFF holding the digital library is able to send to DAS both a reference to the priority document and some applicant contact information (either physical mailing address or e‑mail address);
(b) Route B: The OFF is able to send to DAS a reference to the priority document, but no further details until the applicant approaches the DAS directly with an access control code which has been assigned; or
(c) Route C: The OFF is not able to send any information at all to DAS until the applicant gives DAS an access control code recognized by the OFF. Under this option, a confirmation of availability can only be provided to the applicant by DAS once availability has been confirmed with the OFF, implying delays in such feedback if DAS and the OFF in question do not have a dedicated real‑time mechanism in place to support the confirmation.
9. The flows of data required are shown in Figures 2 to 4. In each case, the applicant will have an access control code sent (or confirmed, if one has already been specified by the applicant) either by the OFF or by DAS. Using Route A, DAS will be able to confirm to the applicant that the system has correctly recognized the priority document. Using Routes B and C, the confirmation may only be possible at a later time than under Route A, namely, when the applicant first submits the code to DAS to manage the access list since prior to that time, the system may have no record of the application, or else insufficient information to activate the access control code within DAS.
Security of delivery
10. The security of the system also requires that the identity of Offices offering digital libraries or attempting to access a priority document be confirmed. However, this does not require special consideration because, whereas the identity of a person claiming to be an applicant is difficult to verify, the Offices involved are a limited group with which the International Bureau already has trusted communication channels. Each of the systems which are proposed to be used for communications already includes a means for establishing a secure channel between the International Bureau and a point which can be identified as a particular Office.
Figure 2
Figure 3
Figure 4